Introducing Android.Spy.510.
Once this malware infects a device, it will retrieve user and device information such as the following and then sends it to a command and control server:
- the user's Google Play account Login and Password
- Mobile device model
- the operating system's SDK version
- Availability of Root Access on the device
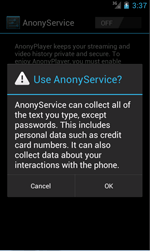
After getting information from the infected device, Android.Spy.510 tries to install an additional hidden program package which is an advertising module(Adware.AnonyPlayer.1.origin) onto the infected device by displaying a text message onscreen.
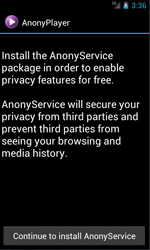 |
| Android.Spy.510's attempt to install Adware.AnonyPlayer.1.origin |
When users proceed to install Android.Spy.510's additional app, they actually download Adware.AnonyPlayer.1.origin.
What does Adware.AnonyPlayer.1.origin do?
This malware disguises itself as an app that makes the user anonymous but only actually just displays advertisements on the infected device.
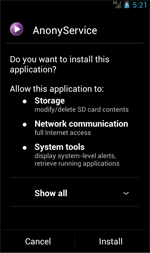 |
| Adware.AnonyPlayer.1.origin's permission's list |
While the user installs the app, the malware sets an incubation period on the infected device's 'Installer_Inc' variable at the SharedPreferences. When the incubation period is over and the app has been installed, the malware will then display advertisements on the infected device.
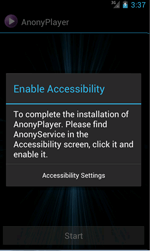
The malware asks the user permission to use the Accessibility Service so that it could monitor all of the infected device's system events.
Adware.AnonyPlayer.1.origin's attempt to enable the Accessibility Service
With the Accessibility Service enabled, Adware.AnonyPlayer.1.origin will be able to determine what program the user launches. The malware will then check if the user has opened/launched an app with a name that corresponds with this list:
- org.adw.launcher
- com.android.launcher
- com.android.systemui
- com.android.settings
- com.android.dialer
- com.huawei.android.launcher
- com.google.android.gm
- com.android.deskclock
- com.android.calendar
- com.android.contacts
- com.sec.android.app.camera
- com.lge.settings.easy
- com.android.providers.downloads.ui
- com.android.calculator2
- com.android.mms
- com.android.phone
- android
- com.lge.clock
- com.sec.android.app.launcher
- com.android.gallery
- com.android.camera
- com.google.android.apps.maps
- com.lge.launcher2
- com.apusapps.launcher
- com.lge.splitwindow
- com.sonyericsson.home
- com.android.incallui
- com.google.android.inputmethod.latin
- com.whatsapp
- com.android.packageinstaller
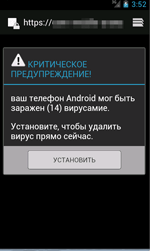 |
| Adware.AnonyPlayer.1.origin's advertisement |
If the user has launched an app whose name is not on the list, the malware will create a special message that uses WebView which contains an advertisement that is downloaded from the command and control server. However, if the launched app is similar to a name on the list, the advertisement function us not activated.
Article Refs: http://vms.drweb.com/virus/?i=7746942(for Android.Spy.510) and http://vms.drweb.com/virus/?i=7746953(for Adware.AnonyPlayer.1.origin)
No comments:
Post a Comment