Android Malware already!
So, what BackDoor malwares are we going to talk about today?
Okay, let's first do a breakdown of our topic for today:
• Android.BackDoor.260 (our main star for today)
• Android.BackDoor.41
• Tool.Substrate.1.origin
• Android.BackDoor.40
• Android.BackDoor.42
• Android.BackDoor.45
• Android.BackDoor.44
• Android.BackDoor.46
• Android.BackDoor.43
• Android.BackDoor.39
Woah! That's a lot! Let's get started already~!
Our main superstar for the night is Android.BackDoor.260.origin. This Trojan was designed to spy on Android users in China(although, this ain't a spyware). It comes as a fake AndroidUpdate app.
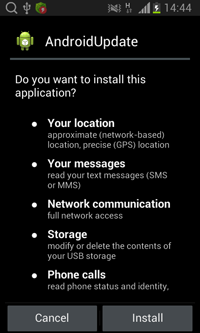 |
| Android.BackDoor.260.origin |
This Trojan extracts the following additional components from its body when it is launched for the first time:
• super
• detect (Android.BackDoor.45)
• liblocSDK4b.so
• libnativeLoad.so (Android.BackDoor.42)
• libPowerDetect.cy.so (Android.BackDoor.39)
• 1.dat (Android.BackDoor.44)
• libstay2.so (Android.BackDoor.43)
• libsleep4.so (Android.BackDoor.46)
• subtrate_signed.apk (Tool.Substrate.1.origin)
• cInstall (Android.BackDoor.41)
After the extraction, this Trojan will attempt to run the cInstall module, aka Android.BackDoor.41, with root privileges. If the Trojan is not successful in having root privileges, the module is run without them. However, if cInstall is successful in acquiring root privileges, it will proceed to install the other additional components into the infected device.
What is Android.BackDoor.41 / cInstall module and what does it do?
First off, Android.BackDoor.41 is an executable UNIX file that runs on Android mobile devices. This is used by Android.BackDoor.260 to install other components on an infected device's system.
This module is responsible for installing the 'super' module into /system/bin; libnativeLoad.so and liblocSDK4b.so into /system/lib; and substrate_signed.apk into the infected device's system.
First off, Android.BackDoor.41 is an executable UNIX file that runs on Android mobile devices. This is used by Android.BackDoor.260 to install other components on an infected device's system.
This module is responsible for installing the 'super' module into /system/bin; libnativeLoad.so and liblocSDK4b.so into /system/lib; and substrate_signed.apk into the infected device's system.
This Trojan(Android.BackDoor.260) will then remove its shortcut from the Home Screen and launches PowerDetectService.
What does PowerDetectService do?
This malicious service monitors the android.intent.action.BOOT_COMPLETED (boot is completed) event and the android.net.conn.CONNECTIVITY_CHANGE (network connectivity change) event. It also runs the substrate_signed.apk module (Tool.Substrate.1.origin) which intercepts all data entered by the user.
This malicious service monitors the android.intent.action.BOOT_COMPLETED (boot is completed) event and the android.net.conn.CONNECTIVITY_CHANGE (network connectivity change) event. It also runs the substrate_signed.apk module (Tool.Substrate.1.origin) which intercepts all data entered by the user.
The PowerDetectService also interacts with libnativeLoad.so library (Android.BackDoor.42) which runs the 'detect' module(Android.BackDoor.45).
This 'detect' file is responsible for activating the libsleep4.so library (Android.BackDoor.46) which takes constant screenshots and also intercepts the user's inputted data as well as the data retrieved by the libstay2.so library (Android.BackDoor.43). This file also runs the 1.dat module (Android.BackDoor.44).
The libstay2.so library (Android.BackDoor.43) steals the infected device's contact list data and monitors all SMS messages and messages exchanged via QQ.
The 1.dat (Android.BackDoor.44) component receives the following commands from the command and control server:
• DOW - downloads a file from the server
• UPL - uploads a file to the server
• PLI, PDL, SDA - updates the malicious modules and their settings
• DIR - gets the list of files on a certain specified folder
• DTK - writes the contents of a specified folder into a file
• OSC, STK - runs a search for a specified file of a folder
• OSF - aborts the search of a specified file
• DEL - deletes a specified file
• SCP - takes a screenshot
• BGS - activates the infected device's microphone and starts to record
• GPRS - activates and tracks GPS coordinates
Sometimes the 1.dat component uses the other malicious libraries to execute the commands given by the command and control server through UNIX sockets by using double-byte commands:
> Executed commands using /data/data/com.sec.android.service.powerManager/cores/audioListener:
• 0x2633 - uses the infected device's microphone and starts recording
• 0x2634 - stops recording
• 0x2635 - updates the configuration file to record audio
> Executed commands using /data/data/com.sec.android.service.powerManager/cores/smsListener:
• 0x2629 & 0x2630 - copies the user's contact list
• 0x2631 - copies the user's SMS messages
• 0x2632 - copies the user's call logs
> Executed commands using /data/data/com.sec.android.service.powerManager/cores/location:
• 0x2628 - forwards the infected device's location information to the Malware Dev
• 0x2532 - forwards the infected device's process name of the currently used application to the Malware Dev
> Executed commands using /data/cores/Users/All Users/Intel/Data/plugin2IPC:
• 0x2678 - uploads all data entered by the user to the server
In order to retrieve the infected device's GPS coordinates, the Trojan uses Baidu Maps for Android which stores all data locally on the infected device. If necessary, the Malware Dev will retrieve the information using some of the listed commands above.(ex: UPL, DIR, etc)
Lastly, Android.BackDoor.260's libPowerDetect.cy.so module (Android.BackDoor.39) intercepts these methods using MSJavaHookMethod from Tool.Substrate.1.origin to log every entered text by the user:
• android.view.inputmethod.BaseInputConnection.commitText(CharSequence text, int newCursorPosition)
• android.inputmethodservice.InputMethodService.onFinishInput()
• android.inputmethodservice.InputMethodService.onWindowHidden()
What is Tool.Substrate.1.origin?
Tool.Substrate.1.origin is a utility that helps expand the functionality of various applications. When installed, this program does not create a shortcut/app icon on the device's Home Screen. Although not originally designed to be malicious on its own, Malware Developers have modified this file and incorporated a new version of it into Android.BackDoor.260.origin, used to intercept data entered by the user. Also, this tool's digital signature is different from the signature of the real program.
Tool.Substrate.1.origin is a utility that helps expand the functionality of various applications. When installed, this program does not create a shortcut/app icon on the device's Home Screen. Although not originally designed to be malicious on its own, Malware Developers have modified this file and incorporated a new version of it into Android.BackDoor.260.origin, used to intercept data entered by the user. Also, this tool's digital signature is different from the signature of the real program.
Article Refs: http://vms.drweb.com/virus/?_is=1&i=7427212 (Android.Backdoor.260), http://vms.drweb.com/virus/?_is=2&i=7428352 (Android.BackDoor.41), http://vms.drweb.com/virus/?_is=1&i=7429979 (Tool.Substrate.1.origin), http://vms.drweb.com/virus/?_is=2&i=7429469 (Android.BackDoor.40), http://vms.drweb.com/virus/?_is=1&i=7429700 (Android.BackDoor.42), http://vms.drweb.com/virus/?_is=1&i=7429852 (Android.BackDoor.45), http://vms.drweb.com/virus/?_is=1&i=7429748 (Android.BackDoor.44), http://vms.drweb.com/virus/?_is=1&i=7429978 (Android.BackDoor.46), http://vms.drweb.com/virus/?_is=1&i=7429726 (Android.BackDoor.43), and http://vms.drweb.com/search/?q=Android.BackDoor.39 (Android.BackDoor.39)
No comments:
Post a Comment